IT Cybersecurity

If you have ever wondered how safe your business or organization would be against a potential cybersecurity attack, we can provide you with reliable answers. 
Our cybersecurity team can help you quickly identify, assess, remediate, and improve cybersecurity effectiveness for your business or organization. We can perform penetration testing, phishing simulations, vulnerability detections and assess to what extent a ransomware attack may be possible. Our team can test the strength and effectiveness of your antivirus, firewalls and more. We further provide IT security audits and security awareness training.
Our security experts can help you develop custom solutions based on your specific needs and methodologies. We are well-versed in the industry's best practices for developing comprehensive security programs and managing the risk-based security outcomes.
Absolute Access ID has partnered with the industry's top cybersecurity experts to provide complete and comprehensive security assessments.
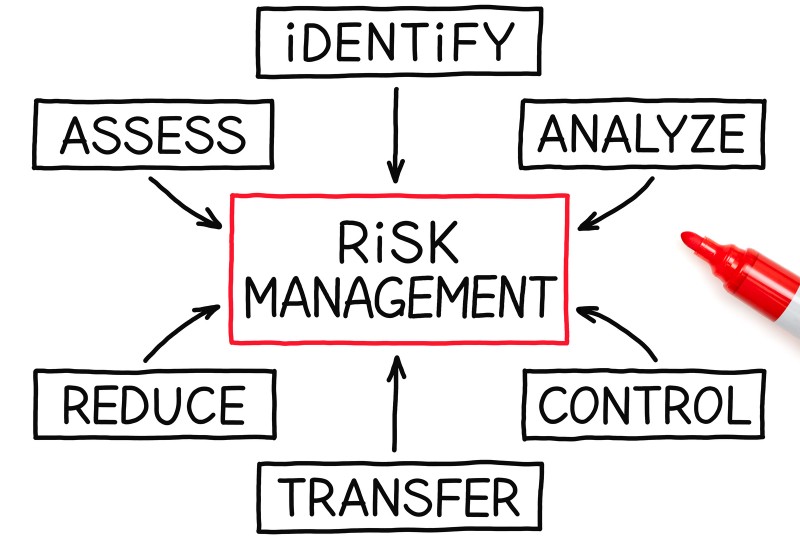 Risk Management: To properly manage your risk, you must be able to see where potential risks are in your environment. By fully understanding these risks, you can increase your network security, reduce your management costs and achieve full compliance. Failing to assess and mitigate IT risk will leave your business or organization open for serious security breaches and financial losses in the future.
Risk Management: To properly manage your risk, you must be able to see where potential risks are in your environment. By fully understanding these risks, you can increase your network security, reduce your management costs and achieve full compliance. Failing to assess and mitigate IT risk will leave your business or organization open for serious security breaches and financial losses in the future.
Compliance: Dealing with compliance requirements can hinder businesses from focusing on business goals. Our team of  experts can locate compliance short falls and quickly provide remediation. Our experts are trained in the latest compliance and regulatory mandates to effectively offer your business a swift solution.
experts can locate compliance short falls and quickly provide remediation. Our experts are trained in the latest compliance and regulatory mandates to effectively offer your business a swift solution.
Phishing: We can test, train and evaluate the security practices of your employees by simulating realistic cyber-attacks. Knowing any potential vulnerabilities and seeing them from a potential hacker's perspective is one of the most valuable insights to properly protecting your security and environment.
Auditing: Our auditing tools can fully evaluate your network devices such as firewalls, routers and switches to locate unknown vulnerabilities and show you how to fix them. Our detailed reports provide rapid resolutions to allow for your IT security team to harden and protect your system to block potential attackers.
 Internet of Things (IoT) Evaluations: We further provide solutions to protect your business and organization by securing your IoT devices from breaches and suspicious activity. It is estimated that millions of connected devices have little to no defense against potential hackers who want to gain control of them. Our team of security professionals can assist in determining your level of vulnerabilities and then provide security solutions to protect your devices from potential hackers.
Internet of Things (IoT) Evaluations: We further provide solutions to protect your business and organization by securing your IoT devices from breaches and suspicious activity. It is estimated that millions of connected devices have little to no defense against potential hackers who want to gain control of them. Our team of security professionals can assist in determining your level of vulnerabilities and then provide security solutions to protect your devices from potential hackers.
Contact us for a no obligation demo on how we can help protect you.
